
|
|||
|
| Home |
| About |
| Hobbies |
| Software |
| Hardware |
| ICT Hotlist |
| Purpose |

About Johan van Soest

Ing. Johan van Soest CIPM is:
- Business Continuity Manager / Data Protection Officer
- Analytical
- Creative
- Out of the box thinker
- Good mood & humor
- High sense of responsibility
- Decisively even during failures and disasters

Motto
I strive towards structured, standardized, redundant, stable ICT-solutions with the best possible service for internal and external customers bound by policy, possibilities and budgetPersonal Data is protected by continuously improving the Availability and Integrity of data and increasing Confidentiality (CIA triad) through technical and organisational measures (training, awareness, encryption, anonymization and procedures)
..:: Certified Information Privacy Manager ::..
The CIPM is the world's first and only certification in privacy program management. When you earn a CIPM, it shows that you don't just know privacy regulations-you know how to make it work for your organization. In other words, you're the go-to person for day-to-day operations when it comes to privacy. The IAPP's CIPM, CIPP/E, CIPP/US and CIPT credentials are accredited by the American National Standards Institute (ANSI) under the International Organization for Standardization (ISO) standard 17024: 2012. Since 2018 the IAPP credentials received global recognition by the International Accreditation Forum Multilateral Recognition Arrangement and ANAB-accredited...:: Hardware ::..
The computer science education sector 'Hardware' does not only include the Hardware design of a computer (see computerarchitectuur) but also includes peripherals, analog and digital (a- and synchronous sequential) circuits with and without local intelligence..:: Software / Programs / Programming ::..
Software education within the computer science education can be divided into:- Micro programs: This is software that is contained in a processor and describes the actions to perform one instruction (For example a sum of two numbers)
- Software that is essential for computers to enable them to perform tasks. Examples are firmware (as in the PC BIOS) and Operating Systems (see Operating Systemen) such as DOS, Windows, UNIX and Linux.
- Drivers for the management of interfaces
- Software needed to let a user perform his/her business tasks. One can think of Word processors, spreadsheets, Databases (see BestandsOrganisatie)
- Parallelism
- Atomic transactions
- Deadlocks
- Semaphores
- Proven correctness
- Data structures (lists, trees etc.)
..:: ComputerArchitectuur ::..
Computer architecture is the course that educates the designing of computers. It includes:-
- The working of the processor
- The working and design of the processor circuits (ALU, busses, timing etc.)
- Memory mapping.
- The design of the memory addressing and the control of computer memory modules
- Input/Output mapping
- The placement of Input/Output circuits and addressing (memory or I/O based) and their connection (DMA, Programmed I/O, Interrupt I/O)
- Input/Output device selection
- Selection of interface devices that are needed for the requested/required application functionality
- The working of the processor
..:: Interfacing ::..
The connection between computers and between computers and periferals. These are all the devices used to convert electrical signals to and fro the computer. One can think of printers, robot arms, sound- and video cards, modems, computer networks etc....:: ComputerNetwerken ::..
The course Computer networks lectures the communication between computers, between computers and peripherals and communication with digitizing equipment. It builds on the knowledge gained with the courses Telecommunication and Datacomunication. The main topics include:- LAN (topologies: Bus, Ethernet, star, ring Token ring, WiFi), WAN
- PSDN (Public-Switched Data Network), PSTN (Public-Switched Telephone Network)
- Communication media (shielded) twisted pair, coax, glass fiber, ether (transmitters, satellite)
- Serial, modem communication standards and working
- Datatransmissionprotocols (TCP/IP IPX/SPX)
- Error detection: parity, CRC etc
- ISO OSI model
..:: SysteemOntwerp ::..
The course software engineering, aims at the difficulties that arise when constructing large programs. It builds on the informatics knowledge together with the organizational management and psychological knowledgeThe course software engineering is structured as a theoretical study and two practices. The solution strategy has the following stages:
- Requirements definition
- Specification
- Design
- Implementation
- Testing
- Maintenance and support
..:: OperatingSystemen ::..
The Operating System (MS-DOS, MS-Windows, Linux and Unix are some well known "OS'ses) is a program that has the purpose to create a workspace to enable the users to execute programs and process and store data. The main purpose is ease of use, the secondary purpose is efficient usage of the computer hardware. During the TCK education, the main attention is to single/multi-user and single/multiprocessor operating systems, disk/file organization and semaphores...:: DataCommunicatie ::..
The TCK course data communication teaches the technologies that are required when (a- and synchronous) digital signals are being transmitted over analog telecommunication media (ether, glass fiber, cable). Main points of interest are:- Error detection, noise
- Sampling
- Coding
- Modulation of digital signals (Pulse code modulation, Frequency Shift Keying, Phase Shift Keying)
- Time Division Multiplexing
- Filters
- PLL's
..:: RegelTechniek ::..
In the course Process Control of the TCK education both analog and discrete process control is teached.Points of interest include:
- Mathematical modeling
- P/I/D controllers
- Discrete process controllers and the impact of sample frequency
- Nonlinear systems
..:: CompilerBouw ::..
The course Languages and Compiler Construction teaches the mathematical description of several regular languages on which compilers are constructed. A compiler is a program that reads programs written in a certain source language and converts it to a target language that can be executed on specific hardware. The main tasks of a compiler are the translation process and the generation of error messages and warnings when the source language (program) does not complies with the syntax of the programming language...:: DataBases ::..
The TCK course Databases consists of:- Relational algebra
- Keys
- Normalisation
- Query languages for maintenance and use (SQL)
- Database models
- Relational
- Network
- Hierarchical
..:: BestandsOrganisatie ::..
This course teaches everything needed to create an optimal solution for a given problem (create, maintain or query databases). This way one can make an educated decision to:- Setting up databases
- Structure databases
- The method of storing data on disks
..:: Recovery Time Objective ::..
A definition of the amount of time it takes, from initial disaster declaration, to having critical business processes available to users. Although automation greatly contributes to enabling low RTO, this metric can't be quantified mathematically...:: Recovery Point Objective ::..
A definition of the amount of data loss that's deemed acceptable, defined by application, in the event of a disaster-failover scenario. This can be from zero to minutes or hours depending on the criticality of the data. It's a definition that can be quantified by an examination of a given I/O profile, the available bandwidth linking the primary and recovery sites, and the applications tolerance to latency."..:: Log shipping ::..
Log shipping is one of the failover solutions offered by Microsoft SQL Server.Failover means substituting a primary server with a backup (sometimes also referred to as standby) server if the primary hardware becomes unusable. To keep the data current and to minimize risk of data loss the process ships, on a continuous basis, SQL Server transaction log backups to the standby SQL Server and automatically restores them to the database. Log Shipping can be used to provide close to 100% uptime
..:: TFA ::..
Two Factor Authentication.Two-factor authentication is a security process in which the user provides two means of identification, one of which is typically a physical token, such as a card, and the other of which is typically something memorized, such as a security code. In this context, the two factors involved are sometimes spoken of as something you have and something you know.
..:: BCM ::..
Business Continuity Management.A holistic management process that identifies potential threats to an organization and the impacts to business operations that those threats-if realized-might cause, and which provides a framework for building organizational resilience with the capability for an effective response that safeguards the interests of its key stakeholders, reputation, brand, and value-creating activities.
![[Courses for the University of Professional Education in Eindhoven with a specialization in Technical Computer Science]](../image/tckcol4.png)
Courses for the University of Professional Education in Eindhoven with a specialization in Technical
Computer Science. Hover the mouse over the image to get more information)
To complement this education, he studied relevant courses at the Technical University of Eindhoven. He especially liked the social orientated courses and the team based courses. That his interests are not limited to technical issues, is shown by the fact that he also managed to complete, with success, the Management education for technicians in Utrecht (The Netherlands)
| Management and Organisation | Communication |
| Strategic Management | Commercial Management |
| Leadership | Personal skills |
| Personnel Management | Change Management |
To support the necessary legal knowledge about the on May 25th 2018 enforced European privacy laws, the General Data Protection Regulation (GDPR), Johan is certified as Information Privacy Manager (CIPM). CIPM is the world's first and only certification in privacy program management.
Earning a CIPM, shows that the holder don't just know privacy regulations-he know how to make it work for an organization. In other words, He is the go-to person for day-to-day operations when it comes to privacy.
The IAPP's CIPM, CIPP/E, CIPP/US and CIPT credentials are accredited by the American National Standards Institute (ANSI) under
the International Organization for Standardization (ISO) standard 17024: 2012.
This internationally recognized certification is managed by the IAPP (International Association of Privacy Professionals) Since 2018 the IAPP credentials received global recognition by the International Accreditation Forum Multilateral Recognition Arrangement and ANAB-accredited.

Brief career description
Johan was employed at the ICT - Department of a global operating leading company that designs, produces, sells and distributes household goods. There he started programming and supporting the mainframe software for manufacturing (MRP, purchasing, calculation, planning, inventory management), logistics and sales. Next he worked as a system designer for these ERP applications and was responsible for the Mainframe Management (3 mainframe operators). Because of his advice to standardize on one platform for software development and network management, significant costs could be saved on network management and expensive mainframe licenses and accompanying expensive hardware upgrades. Realising an immediate cost saving of 1.5 million guilders and additional yearly savings on expensive Mainframe licenses. After having successfully managed the large network and mainframe migration projects, Johan was employed as Business Continuity Manager (BCM) and ICT - Specialist within the same company. In this role the groupleaders and ICT-Manager are coached in organizing, describing, configuring and testing disaster recovery procedures concerning the worldwide ICT services. Modifications and investments are assessed against possible consequences for disaster recovery, and high availability of the final solution. Given the constant introduction of new technologies, trends and services a continuous improvement process (Deming) is set up, so the changes are consolidated in standardized procedures.
![]() Johan was also the technical Webmaster of the company web-sites, purchased the international domain registrations and took care that partners and importers were supported configuring their webshops.
The brand was being protected on the internet with the use of the Trademark Clearinghouse (TMCH) and support of the sales directors.
Johan was also the technical Webmaster of the company web-sites, purchased the international domain registrations and took care that partners and importers were supported configuring their webshops.
The brand was being protected on the internet with the use of the Trademark Clearinghouse (TMCH) and support of the sales directors.
Given the positive results of the BCM role, Johan was asked by management in 2017 to assume the role of Data Protection Officer FG / DPO of the General Data Protection Regulation (AVG / GDPR). In 2018 he has achieved the world renowned IAPP
CIPM certification.
The Data Protection Officer (DPO) is a mandatory or voluntarily appointed independent supervisor and advisor within an organization for the General Data Protection Regulation (GDPR).
The DPO makes an important contribution to the careful, safe and lawful use of personal data by an organization and engaged service providers and also provides information and advice on the obligations under privacy legislation, cooperates with the Data Protection Authority and represents the interests of Data Subjects.
An DPO converts abstract privacy laws into practically applicable advice for the organization concerned, provides support, instructions and training for employees and advises on the part of the GDPR in contracts of customers and suppliers. Optimizing the Confidentiality, Integrity and Availability (CIA) of personal data by introducing and testing technical and organizational measures is an objective.
One of the duties of the Data Protection Officer is to educate colleagues about the GDPR and raise awareness about security and confidentiality. With the same tooling, Johan provided Security and Phishing training for all colleagues worldwide. This included managing and motivating learners to complete the courses on time and actually support them in the learning process.
ICT renews itself so quickly with new concepts and technologies so "lifelong learning" consisting of a solid education supplemented by product-oriented courses and through professional literature is required. A complete list of courses can be found here (Partially in Dutch).
Successful projects
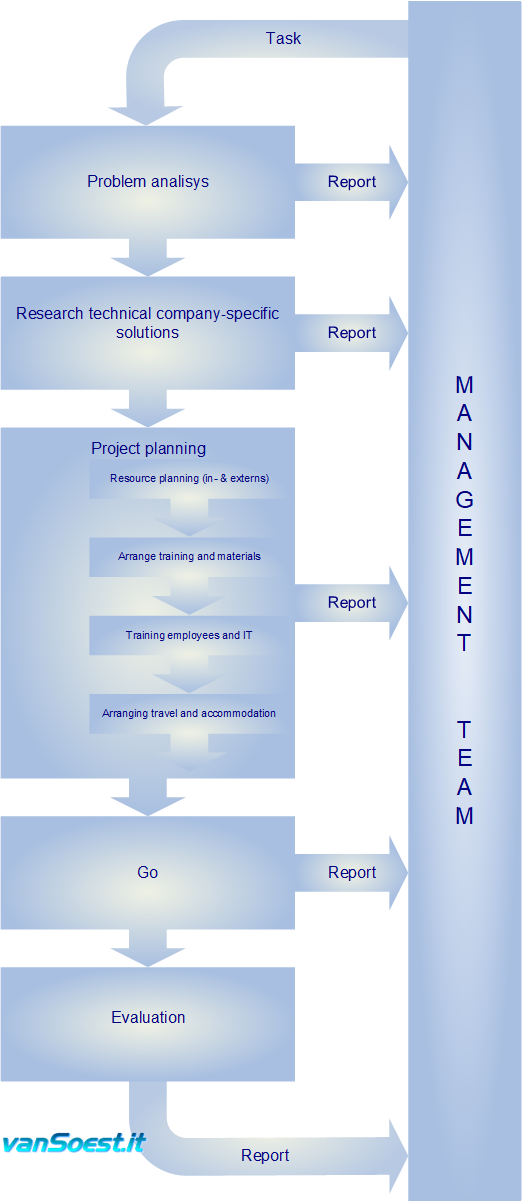
Project steps.
- Johan has managed several large IT migration projects. These projects include the complete cycle:
-
![[*]](../image/ornamnta.gif) Problem inventory
Problem inventory
-
![[*]](../image/ornamnta.gif) Researching Technical and Business specific solutions
Researching Technical and Business specific solutions
-
![[*]](../image/ornamnta.gif) Project planning
Project planning
-
![[*]](../image/ornamnta.gif) Resource planning (in- and external) including training of employees and IT-staff
Resource planning (in- and external) including training of employees and IT-staff
-
![[*]](../image/ornamnta.gif) Arranging travel and stay
Arranging travel and stay
-
![[*]](../image/ornamnta.gif) Implementation
Implementation
-
![[*]](../image/ornamnta.gif) Evaluation
Evaluation
- One of the strategies was to reduce the number of operating systems supported by the ICT - department. Subprojects included:
-
![[*]](../image/ornamnta.gif) Migration of worldwide Novell Netware
network to Microsoft Windows Active directory
Migration of worldwide Novell Netware
network to Microsoft Windows Active directory
-
![[*]](../image/ornamnta.gif) Migration of worldwide Novell GroupWise
to Microsoft Exchange mail services
Migration of worldwide Novell GroupWise
to Microsoft Exchange mail services
-
![[*]](../image/ornamnta.gif) Migration of complete logistical system from the Unisys mainframes to
Microsoft Windows Enterprise servers
on Microsoft SQL Enterprise databases with the
LION toolset. Realising an immediate cost saving of 1.5 million guilders.
Migration of complete logistical system from the Unisys mainframes to
Microsoft Windows Enterprise servers
on Microsoft SQL Enterprise databases with the
LION toolset. Realising an immediate cost saving of 1.5 million guilders.
-
![[*]](../image/ornamnta.gif) Migration of all the ERP software to a High Availability platform with a hot standby location.
The platform is based on Active-Active Microsoft SQL clustered databases and redundant Application servers for the business logic.
The storage technology is based on HP StorageWorks Enterprise Virtual Array and
HP StorageWorks Modular Smart Array
Migration of all the ERP software to a High Availability platform with a hot standby location.
The platform is based on Active-Active Microsoft SQL clustered databases and redundant Application servers for the business logic.
The storage technology is based on HP StorageWorks Enterprise Virtual Array and
HP StorageWorks Modular Smart Array
- Other successful projects include:
-
![[*]](../image/ornamnta.gif) Implementing EDI shipment carrier information in the logistical system
Implementing EDI shipment carrier information in the logistical system
-
![[*]](../image/ornamnta.gif) Introducing ITIL
Introducing ITIL
This was an important organizational change for the IT-Department and it introduced the:- New first-line knowledgeable ICT-helpdesk with ticketing system
- Defined second and third-line support levels using in-house expertise and suppliers
- Configuration management database CMDB
- Change Management
-
![[*]](../image/ornamnta.gif) Business Continuity Management: Reshaping the ICT - infrastructure (hardware, software, interfacing
and synchronizing) and awareness for establishing a company owned Business Continuity room that
fully mirrors the primary location. (RTO = 48 hrs,
RPO = 24 hrs)
Business Continuity Management: Reshaping the ICT - infrastructure (hardware, software, interfacing
and synchronizing) and awareness for establishing a company owned Business Continuity room that
fully mirrors the primary location. (RTO = 48 hrs,
RPO = 24 hrs)
-
![[*]](../image/ornamnta.gif) Virtualizing the Microsoft SQL Server Enterprise databases and
LIONDev based ERP applications on the VMware ESX platform on
HP StorageWorks Enterprise Virtual Arrays (SAN) with compressed
Log shipping
Virtualizing the Microsoft SQL Server Enterprise databases and
LIONDev based ERP applications on the VMware ESX platform on
HP StorageWorks Enterprise Virtual Arrays (SAN) with compressed
Log shipping
-
![[*]](../image/ornamnta.gif) Relocation of the ICT - Department, computer centre and employees because of the imminent demolition of
the offices. This required the Business Continuity room to be fully operational, data traffic rerouted
and all pc's to be reconfigured for the new location. In a weekend the Business Continuity procedures
and configurations Johan developed were executed and the systems were fully operational the next working
day without any downtime and loss of data. Next the employees could be relocated to their new offices.
Relocation of the ICT - Department, computer centre and employees because of the imminent demolition of
the offices. This required the Business Continuity room to be fully operational, data traffic rerouted
and all pc's to be reconfigured for the new location. In a weekend the Business Continuity procedures
and configurations Johan developed were executed and the systems were fully operational the next working
day without any downtime and loss of data. Next the employees could be relocated to their new offices.
-
![[*]](../image/ornamnta.gif) After the product comparison, risks and benefits assessment the management team
has decided to migrate the LIONDev based ERP applications from the 32 bit Delphi platform
to the Microsoft.net c# platform using
AMT-LION.
The Application, Reporting and Database servers run
on Windows 2008R2 (64 bit) utilizing the Microsoft SQL Server 2008R2 databases.
In addition to the modernization of the deployment platform, this will make Unicode
support (among other Baltic and Asian fonts) and graphical tools available to the
ERP development group.
After the product comparison, risks and benefits assessment the management team
has decided to migrate the LIONDev based ERP applications from the 32 bit Delphi platform
to the Microsoft.net c# platform using
AMT-LION.
The Application, Reporting and Database servers run
on Windows 2008R2 (64 bit) utilizing the Microsoft SQL Server 2008R2 databases.
In addition to the modernization of the deployment platform, this will make Unicode
support (among other Baltic and Asian fonts) and graphical tools available to the
ERP development group.
Johan played a major role in this project developing a Business Continuity and upgrade strategy, preparing the servers, services and databases, rolling out the client software and resolving migration issues. -
![[*]](../image/ornamnta.gif) Upgrading and migrating the worldwide Windows network with the Windows 2008 R2 64 bits server
architecture. Focus is directed to the "New working style" (anyplace,
anytime and anywhere), but in a safe manner.
Upgrading and migrating the worldwide Windows network with the Windows 2008 R2 64 bits server
architecture. Focus is directed to the "New working style" (anyplace,
anytime and anywhere), but in a safe manner.
To increase disk capacity Sun/Oracle SAN's were introduced. With the added disk capacity it is possible to utilize the versioning and undelete functionality of the Windows 2008R2 platform. This increases end-user efficiency as they are, most of the time, able to restore previous versions of a document or undelete a document on the file servers by themselves. Activation of Microsoft Office 2010 and Windows 2008R2 servers is managed with the Microsoft Volume Activation Management Tool (VAMT) -
![[*]](../image/ornamnta.gif) After an extended comparison of several application and desktop virtualisation products, it was decided to
replace and migrate the Citrix Presentation Server environment to the
Windows 2008 R2 Server Citrix XenApp 6.5
environment using the Citrix Secure Gateway 3.3.
Two Factor Authentication is implemented by using Yubikey
OTP tokens.
After an extended comparison of several application and desktop virtualisation products, it was decided to
replace and migrate the Citrix Presentation Server environment to the
Windows 2008 R2 Server Citrix XenApp 6.5
environment using the Citrix Secure Gateway 3.3.
Two Factor Authentication is implemented by using Yubikey
OTP tokens.
-
![[*]](../image/ornamnta.gif) Replacing LibreOffice with Microsoft Office 2013 (Word, Excel, PowerPoint, Outlook and OneNote) also within the Citrix XenApp environment.
Replacing LibreOffice with Microsoft Office 2013 (Word, Excel, PowerPoint, Outlook and OneNote) also within the Citrix XenApp environment.
-
![[*]](../image/ornamnta.gif) The integration of a foreign production unit into the company domain. This required a design that confirms to the Business Continuity strategy that Johan designed.
The integration of a foreign production unit into the company domain. This required a design that confirms to the Business Continuity strategy that Johan designed.
-
![[*]](../image/ornamnta.gif) Improved supply chain management. With the Citrix portal suppliers get an overview of the production planning of products containing their
articles. This project gives external suppliers access to the company network and core applications making it necessary to increase the
application and network security.
Improved supply chain management. With the Citrix portal suppliers get an overview of the production planning of products containing their
articles. This project gives external suppliers access to the company network and core applications making it necessary to increase the
application and network security.
-
![[*]](../image/ornamnta.gif) Managing "mode 2" ICT-projects (Gartner 2014 Bimodal IT / Bipolar IT) to improve ICT-Services. These include:
Managing "mode 2" ICT-projects (Gartner 2014 Bimodal IT / Bipolar IT) to improve ICT-Services. These include:
- New e-Mail infrastructure / Collaboration platform resulting in an Office 365 implementation. Successfully completed.
- PKI infrastructure. Implemented using Windows PKI. Successfully completed.
- Upgrade Forest/Domain levels to Windows 2016 servers. Successfully completed.
- Mobile Device Management (MDM) to support Bring Your Own Devices (BYOD) and/or Choose Your Own Devices (CYOD). Implemented using Office 365.
- New Radius services for Two Factor Authentication (TFA). Implemented using Office 365 authentication.
- Upgrading to a worldwide AntiVirus/AntiSpam solution. Successfully completed.
- Desired State Configuration resulting in a PowerShell software deployment script. Successfully completed. To be upgraded to Microsoft Endpoint Configuration.
Other tasks
- Next to the continuing BCM task, Johan worked on the following tasks:
![[*]](../image/ornamnta.gif) Managing the world wide Privacy program.
Managing the world wide Privacy program.
![[*]](../image/ornamnta.gif) Office 365 migration limited to Security, Privacy and DLP (Data Loss Prevention)
Office 365 migration limited to Security, Privacy and DLP (Data Loss Prevention)
![[*]](../image/ornamnta.gif) Webmaster
Webmaster
![[*]](../image/ornamnta.gif) Privacy, Security and Phishing trainer.
Privacy, Security and Phishing trainer.

